Chapters
How to Secure Your Crypto Portfolio Against Hacks & Scams
Protecting your crypto holdings has never been more critical. With over $2.17 billion already stolen in crypto hacks during the first half of 2025, and personal wallet compromises accounting for nearly 23% of that theft, if you're serious about long‑term success, security isn’t optional; it’s foundational.
Here’s a full, layered guide to a secure crypto portfolio to help your assets stay safe and your mind stay relaxed.
1. Use Cold Wallets for Long-Term Storage
When thinking “how to secure crypto portfolio,” your first move should be cold (offline) wallets. These hardware wallets, like Ledger, Trezor, Tangem, CoolWallet Pro, and Keystone, hold the majority of your assets offline and are nearly immune to online attacks.
Cold wallet cards are booming: in Q2 2025, over $3.8 billion in crypto sat on hardware wallets, with card formats growing rapidly.
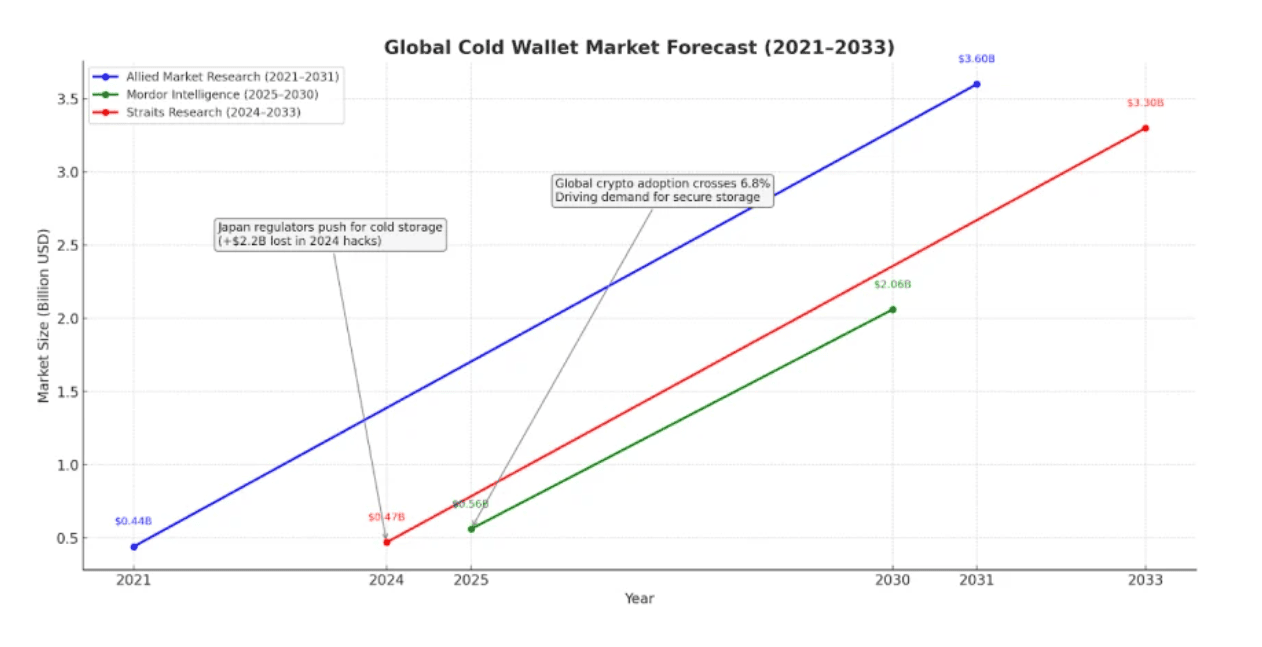
Source: Antier Solutions
Meanwhile, hot wallets (online/mobile) make up about 78% of wallets, but are far more vulnerable.
Keep only small trading sums in hot wallets; everything else goes offline.
2. Enable Two-Factor Authentication (2FA)
A strong password plus 2FA is non‑negotiable. Use app‑based authenticators like Google Authenticator, Authy, or Aegis. Never use SMS—SIM-swap scams are on the rise, with reported losses exceeding $150 million globally in 2025.
Where possible, use air‑gapped or hardware-based 2FA (like YubiKey or SoloKey). These don’t rely on your network connection and are immune to phishing attacks and remote hijacks.
3. Backup and Secure Your Recovery Phrases
Never save seed phrases digitally – not in your Notes app, not in Google Drive, not even in a “hidden” folder. Instead:
Write or engrave them on durable materials—steel plates now start under $20 and resist fire, water, and corrosion.
Store backups in different secure locations: a fireproof home safe and a bank safety deposit box is a solid combo.
Never enter your seed phrase online unless you're 100% sure it’s a trusted, offline environment. If a site or app asks for it out of the blue, it’s a scam.
Over 80% of the $2.1 billion stolen in the first half of 2025 came from infrastructure attacks, which include seed phrase and private key thefts.
Source: TRM Labs
4. Use Strong, Unique Passwords
Every crypto platform: wallet, DEX, staking portal needs its own unique, complex password. Use a password manager like Bitwarden, 1Password, or Proton Pass to generate and store them.
Don’t reuse or recycle. Hackers run breach databases with billions of leaked credentials from past years. Some experts now recommend rotating crypto-related passwords every 3–6 months, especially for active accounts.
5. Diversify Your Wallets & Use Multisig
Don’t let a single compromised wallet sink your entire strategy.
Have separate wallets for daily use, long-term holding, and experimental projects.
Use multi-signature wallets (multisig) Gnosis Safe or Sparrow, especially for assets over $10,000: these require multiple private keys to approve a transaction—great for significant holdings.
Even institutional investors now use multisig as a standard layer. If a wallet gets compromised, multisig and wallet segmentation ensure it won’t take down your entire portfolio.
6. Keep Software Updated
Crypto and wallet software are constantly being patched. Staying current with updates, like wallet firmware, apps, browser extensions, or operating systems, closes security holes hackers love to exploit.
In Q2 2025 alone, over 20 zero-day vulnerabilities were discovered across common browser extensions and wallet software. So don’t risk it and set updates to auto-install wherever possible and stay alert for security advisories from wallet developers.
7. Be Cautious With Online Activity
Skip public Wi‑Fi when dealing with assets; consider using a VPN if necessary.
Always bookmark official URLs; phishing sites are now mimicking everything from MetaMask popups to Trezor firmware updates. In 2025, phishing accounted for over 30% of crypto-related breaches, with most victims tricked through fake Google Ads or cloned websites.
Also, never paste private keys or phrases into chats or emails; keyloggers and clipboard malware are stealthier than ever.
8. Only Use Reputable Platforms
Avoid shady exchanges or unverified tokens. Stick with well-known, regulated names like Coinbase, Kraken, Binance, or other vetted platforms.
New platforms without a track record increase your risk exponentially.
9. Watch for Common Scams
Be suspicious of “guaranteed returns”—they almost always mean fraud.
Ignore unsolicited airdropped tokens—they could contain malicious contracts.
No legitimate service will ask for your private keys or demand payment via unsolicited messages.
Fake support teams and Telegram bots continue to impersonate major platforms. No legit service will ever DM you asking for private keys or payment.
Scammers are using AI chatbots and deepfakes to impersonate founders and influencers. Stay skeptical.
10. Educate Yourself and Stay Informed
Security threats evolve fast. Follow trusted sources and crypto advisories to keep up. Chainalysis, TechRadar, security teams at exchanges, and forums like r/CryptoCurrency can help you stay alert.
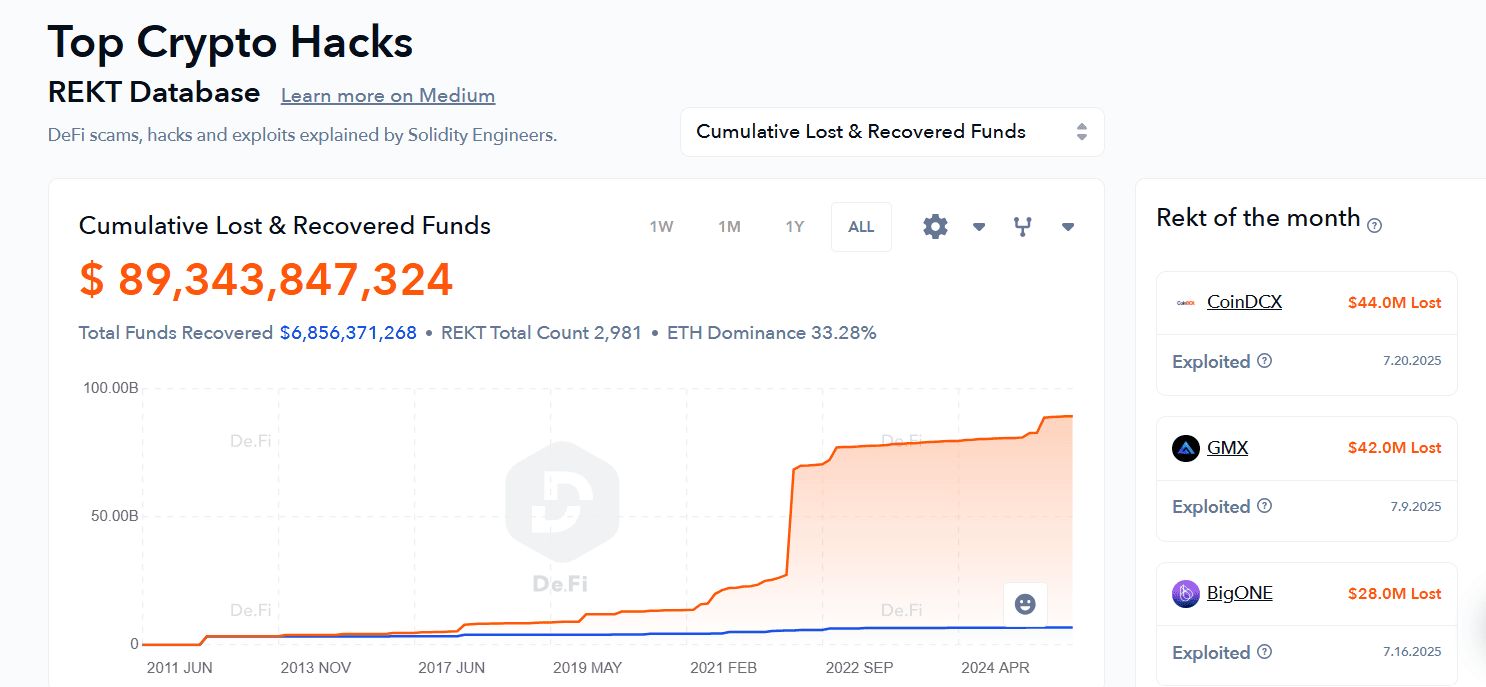
You can also use De.Fi's “Rekt” database to track major hacks and rug pulls.
Being proactive beats being reactive. In crypto, ignorance can have your entire wallet wiped out.
Bonus Strategies for a Secure Crypto Portfolio
Diversify Your Holdings Wisely
A robust portfolio balances major coins, altcoins, and stablecoins. Aim for 40–50% in Bitcoin or Ethereum, with 10–20% in stablecoins for liquidity and risk control. Reserve some investment in emerging alt‑projects, but only after heavy research.
Rebalance Regularly
As markets shift, so do your allocations. Check and rebalance your portfolio quarterly or sooner if volatility is high to keep your asset mix aligned with your strategy.
Use Trackers & Security-Conscious Tools
Portfolio trackers like CoinLedger or other reputable platforms can simplify tracking across wallets and exchanges. Prioritize tools that emphasize strong security practices, like encrypted APIs or non-custodial design.
Prepare for Emerging Threats: Quantum & Future Risks
Quantum computing poses long‑term risks to crypto. Transitioning to post‑quantum cryptographic methods, or choosing wallets with crypto-agility, can future‑proof your assets.
Research wallets with new Threshold Secret Sharing or zero‑knowledge recovery functionality – they’re designed to resist advanced future attacks.
Key Takeaways
A secure crypto portfolio isn’t built overnight. It takes intention, redundancy, and flexibility to evolve with the threat landscape. Combine cold storage, strong access controls, education, and the right tools, so you can build long-term security into your growth plan.























.svg)






